Securing your Devices
Securing your devices is not only simple but also highly effective. Yet, some individuals either fail to grasp its importance or choose to overlook it altogether. Device security involves steps such as using PINs or passwords, locking devices when unattended, timely software updates, and employing antivirus and firewall protection. Let’s delve into each step to understand its significance, proper implementation, and why it’s crucial.
Using PINs/Passwords
Setting up a PIN or password acts as the initial defence against unauthorised access to your device if it were to get lost or stolen. It serves as a barrier, preventing individuals without the correct credentials from accessing your personal information. However, it’s important to create strong and unique PINs or passwords. Avoid common combinations like “1234” or “password,” as well as easily guessable details such as birthdates. Remember, strong credentials enhance security.
Locking Your Devices
Whether in public spaces or at home, locking your devices before stepping away is a good habit. By doing so, you ensure that your data is safer in case of loss or theft. You can manually lock your device or utilise settings to automate the process after a designated period of inactivity. This additional layer of security ensures your personal information remains protected, even when you’re not physically present.
Updating Software
Regular software updates are crucial as they often contain patches for security vulnerabilities exploited by malicious actors. Ensuring your device’s software is up-to-date means you have the latest security fixes installed. You can opt for automatic updates to keep your device secure or manually check for updates periodically. Either way, staying current with software updates helps mitigate the risk of potential security breaches.
Using Antivirus and Firewall

Antivirus software and firewalls provide additional layers of defence against various online threats, including malware and phishing attacks. They monitor incoming and outgoing traffic, detect suspicious activities, and block malicious programs. By employing these tools, you bolster your device’s security against known threats. For example, Windows Defender is included on all Windows operating systems and is a built-in antivirus tool that actively identifies and isolates potentially harmful files, providing real-time protection against malicious software. However, it’s important to note that this doesn’t mean Windows Defender is perfect or enough. Other antivirus programs are still absolutely recommended to complement and enhance your device’s security measures.
Windows Defender Notification
In the illustration below, Windows Defender is actively isolating files flagged as malicious and potentially harmful to the device. These alerts provide crucial information such as the date of detection, details about the program or file, and its severity level. If you encounter such warnings on your device, it’s essential to reconsider the sources from which you download and whom to trust.
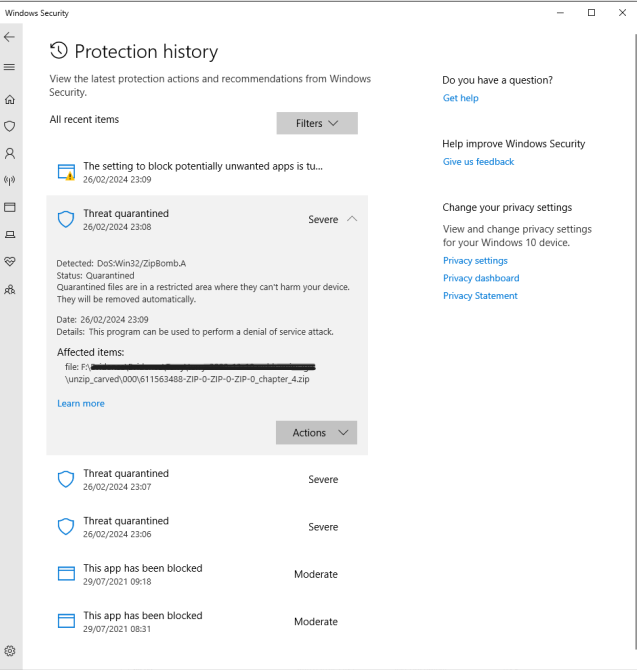
In such instances, it’s recommended to promptly remove the flagged files and restore your system from a previous backup or perform a full device reset. While throwing your device into the depths of the ocean may guarantee 100% safety, it’s perhaps not the most practical approach! So what then? Well, In such cases, seeking assistance from a qualified computer technician is advisable. They can provide expert guidance and assistance in thoroughly addressing any remaining concerns after antivirus scans or device resets.